How Secure is the Bitcoin Network – An In-Depth Exploration of Safety in Cryptocurrency
How secure is the Bitcoin network? This query lies at the heart of discussions surrounding one of the most revolutionary financial systems of our time. As Bitcoin continues to gain traction as a legitimate asset class, understanding its security features and vulnerabilities becomes paramount for investors, developers, and users alike. In this post, we will dive deep into the various aspects that constitute Bitcoin’s security framework.
Bitcoin Network Security: An Overview
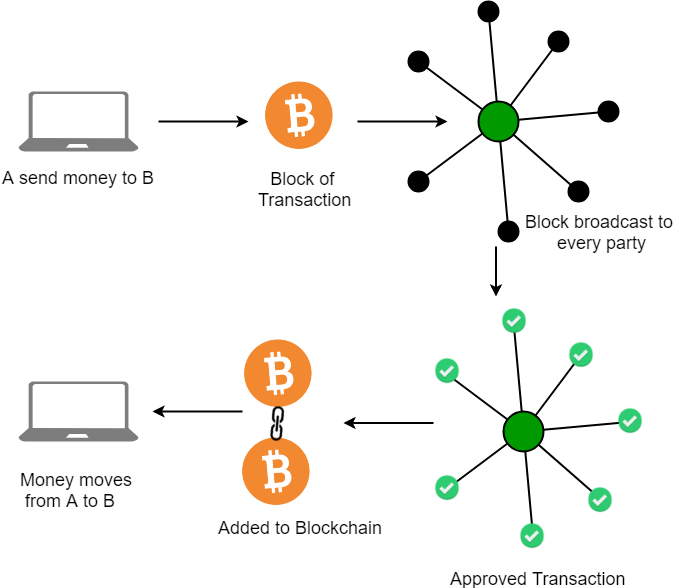
The Bitcoin network represents a groundbreaking shift in how transactions are processed and validated. By operating on a decentralized ledger known as the blockchain, it provides an innovative answer to issues of trust and fraud that have plagued traditional banking systems. However, with this innovation comes a myriad of questions regarding security—both from external threats and internal vulnerabilities.
The Nature of Decentralization
At the core of Bitcoin’s architecture lies decentralization, which means that no single entity has control over the entire network. This structure enhances security by distributing power across thousands of nodes worldwide.
Decentralization eliminates the risk of a single point of failure. If one node goes down, the others continue to operate seamlessly, ensuring that the system remains functional. Moreover, since each participant holds a copy of the blockchain, altering transaction records becomes exceedingly difficult.
However, while decentralization is a strong suit, it also poses challenges. For instance, a user’s experience can depend heavily on the quality and reliability of their chosen node. Thus, while the overall network may be secure, individual experiences can vary greatly.
The Role of Consensus Mechanisms
Bitcoin employs a consensus mechanism known as Proof of Work (PoW) to validate transactions. This process involves miners solving complex mathematical problems to add new blocks to the blockchain.
Proof of Work not only helps secure the network but also makes it resistant to double-spending attacks. Miners compete to solve these puzzles, contributing computational power to maintain the integrity of the blockchain. The requirement of significant resources acts as a deterrent against malicious actors attempting to compromise the network.
Nevertheless, PoW isn’t without its criticisms. The extensive energy consumption required for mining raises ethical concerns, particularly in terms of environmental impact. Additionally, the centralization of mining farms can lead to potential vulnerabilities.
Importance of Transparency and Auditability
One of the key strengths of the Bitcoin network is its transparency. Every transaction is recorded on the public blockchain, making it easy for anyone to audit and verify the history of coins.
This level of transparency fosters trust among users. Since everyone can access the same information, the chances of fraudulent activities decrease significantly.
Moreover, the immutable nature of blockchain ensures that once a transaction is recorded, it cannot be altered or deleted. This feature not only enhances security but also serves as a permanent record for all financial activity.
Cryptographic Foundations of Bitcoin Security
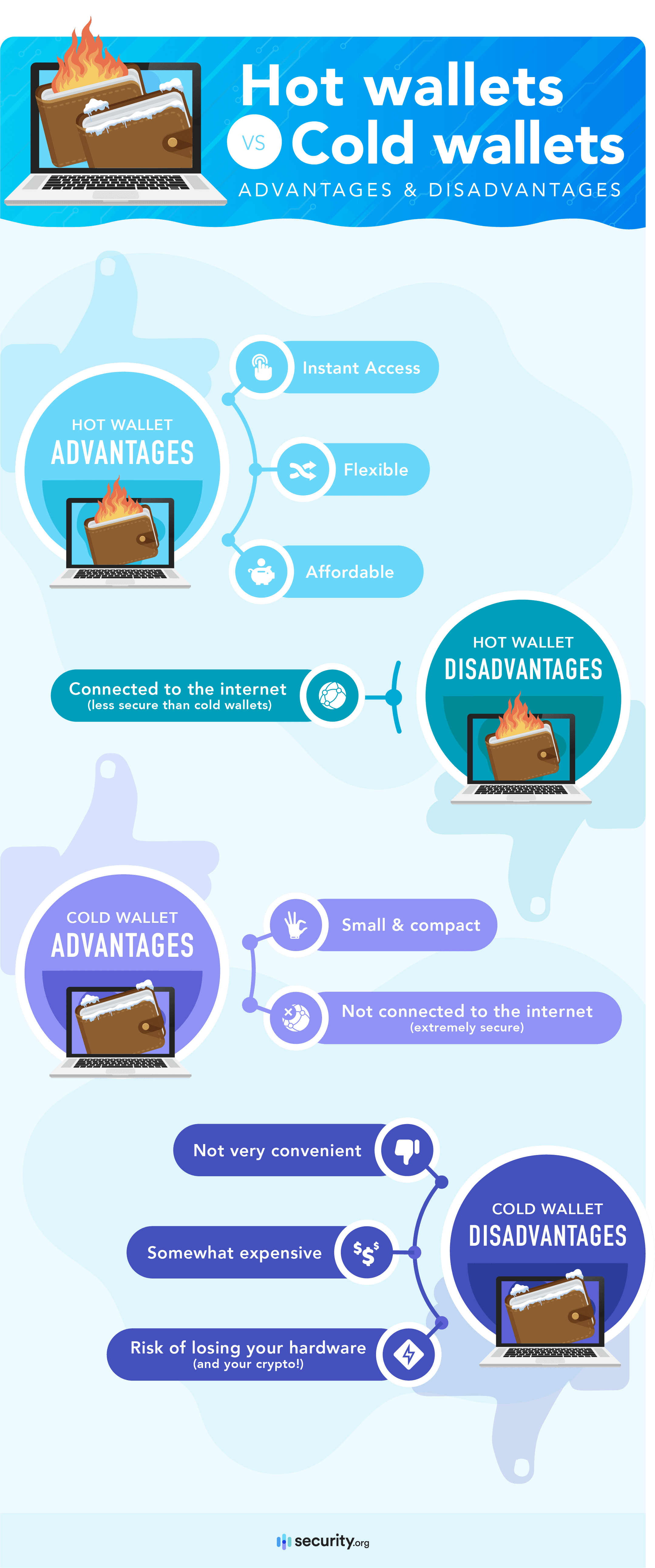
Cryptography is the backbone of Bitcoin’s security architecture. It plays a pivotal role in ensuring the integrity, confidentiality, and authenticity of transactions, making it essential to delve deeper into how these mechanisms function.
Public Key Infrastructure
Bitcoin utilizes a public-key cryptography model that allows users to generate two keys: a public key and a private key.
The public key acts like an address, visible to others who wish to send Bitcoin, while the private key is confidential and must never be shared.
This asymmetric encryption method ensures that even if someone knows your public key, they cannot access your funds without the corresponding private key.
While this system is robust, users must remember that loss of the private key results in permanent loss of access to the associated Bitcoin. This highlights the importance of secure storage solutions, such as hardware wallets, to safeguard private keys.
Hash Functions
Hash functions serve as another critical component of Bitcoin’s security framework. Each block in the blockchain contains a cryptographic hash of the previous block, linking them in an immutable chain.
When a miner adds a new block, it must contain a hash that meets specific requirements, making it computationally expensive to alter any block without redoing the work of all subsequent blocks.
This characteristic makes the Bitcoin blockchain incredibly secure. Even a slight change in transaction data alters the hash, prompting a recalculation of subsequent hashes, thereby alerting the network to potential tampering.
Digital Signatures
Digital signatures further strengthen Bitcoin’s security by providing proof of ownership and consent for transactions. When users initiate a transaction, they sign it with their private key, creating a unique signature that can be verified using their public key.
This process ensures that only the rightful owner of the Bitcoin can authorize its transfer. It also protects against forgery; even if someone obtained a user’s public key, they could not replicate the digital signature without the private key.
The combination of public-private key pairs, hash functions, and digital signatures creates a robust security framework that protects the integrity of the Bitcoin network.
Potential Attack Vectors on the Bitcoin Network
Despite its advanced security measures, the Bitcoin network is not impervious to attacks. Understanding these potential attack vectors is vital for assessing the network’s overall resiliency.
51% Attack
One of the most discussed threats to blockchain networks is the infamous 51% attack. This occurs when a single entity or group of miners gains control of more than half of the network’s hashing power.
With this amount of power, attackers can potentially manipulate the blockchain by reversing transactions, halting payments, and even double-spending coins.
Although the probability of a successful 51% attack diminishes as the network grows—thanks to increasing hashing power—the theoretical risk remains. This challenge prompts ongoing discussions about how to enhance security protocols to mitigate such threats.
Sybil Attacks
Another potential vulnerability is the Sybil attack, where an attacker creates multiple fake identities to gain influence over the network.
In a Sybil attack, the malicious actor can disrupt communication between nodes, leading to misinformation and potential market manipulation.
While Bitcoin’s decentralized structure makes it difficult to execute a large-scale Sybil attack, smaller networks could be more susceptible. Therefore, continuous monitoring and vigilance are crucial to preemptively identify and neutralize such threats.
Distributed Denial-of-Service (DDoS) Attacks
DDoS attacks aim to overwhelm a network with traffic, rendering it unresponsive. Although direct attacks on the Bitcoin protocol are rare, exchanges and wallet services often face DDoS attacks that hinder user access.
These disruptions can cause panic selling and volatility in market prices. While the Bitcoin protocol itself may remain secure, the surrounding infrastructure often proves vulnerable.
Investors should be aware of this risk and consider the security measures implemented by cryptocurrency exchanges before entrusting them with funds.
Mining and the 51% Attack Threat
Mining continues to play a critical role in securing the Bitcoin network, yet it introduces additional complexities regarding security. The relationship between mining, economic incentives, and potential vulnerabilities must be understood to assess risks comprehensively.
Economic Incentives
Miners are incentivized to participate in the network through rewards in the form of newly minted Bitcoin and transaction fees. This system encourages honesty, as miners have everything to lose by attempting malicious activities.
However, as the network matures, the reward structure evolves. The halving events that occur every four years reduce the block reward, consequently impacting miners’ profitability. This situation can lead to centralization, as only those with significant resources can continue to compete effectively.
As miners consolidate their operations in pursuit of cost efficiency, the risk of a 51% attack increases. This paradox illustrates the need for a balanced approach to maintaining decentralization while rewarding participants adequately.
Pool Mining and Centralization Concerns
The rise of mining pools has further complicated the landscape. These groups allow miners to combine their hashing power to increase the chance of successfully mining a block, subsequently sharing the rewards.
While pool mining has democratized access to mining, it also raises concerns about centralization. A dominant mining pool could pose a serious threat to the network if it were to surpass the critical threshold needed for a 51% attack.
Network participants must remain vigilant about the distribution of mining power and advocate for initiatives that promote fair competition.
Technological Solutions for Security Enhancement
To mitigate the risks associated with mining centralization, various technological solutions have been proposed. For example, transitioning to alternative consensus mechanisms, such as Proof of Stake (PoS), could diminish the reliance on mining altogether.
Additionally, developing layers on top of the Bitcoin blockchain, such as the Lightning Network, can facilitate faster transactions and lower congestion—making it less appealing for attackers to exploit the network during peak times.
Investors and users should stay informed about these developments to understand their implications for the security of the Bitcoin network.
Security Enhancements and Ongoing Developments
The landscape of Bitcoin security is continually evolving, as developers and researchers work tirelessly to address emerging threats and vulnerabilities. Here are some recent advancements and ongoing developments aimed at fortifying the network’s defenses.
Layer 2 Solutions
Layer 2 solutions, such as the Lightning Network, are designed to enhance the scalability and speed of Bitcoin transactions.
By enabling off-chain transactions, these solutions allow users to conduct transactions without congesting the main blockchain.
Furthermore, reducing on-chain transactions decreases the potential attack surface, enhancing overall security. By alleviating pressure on the base layer, Layer 2 solutions create a more resilient network that can better withstand various types of attacks.
Multi-Signature Wallets
Multi-signature (multisig) wallets require multiple private keys to authorize a transaction. This added layer of security makes it more difficult for hackers to gain access to funds, as they would need to compromise multiple keys instead of just one.
Multisig wallets are particularly beneficial for organizations and exchanges, where safeguarding funds is paramount. They offer a way to distribute control, thus minimizing the risk of a single point of failure.
Continuous Research and Development
Ongoing research within the cryptocurrency community focuses on identifying vulnerabilities and developing solutions to combat them. Projects like Taproot aim to enhance privacy and scalability, while others explore alternate consensus mechanisms that could improve security.
Furthermore, educational initiatives within the community help raise awareness about best practices for securing funds and recognizing potential threats.
Investors should remain engaged with these developments and actively seek resources that contribute to a better understanding of Bitcoin security.
Assessing the Overall Security of Bitcoin
In evaluating the overall security of Bitcoin, one must consider both its strengths and weaknesses. The intricate balance between decentralization, the economic landscape, and potential vulnerabilities shapes the foundation upon which Bitcoin operates.
Strengths of the Bitcoin Network
Bitcoin boasts numerous strengths that contribute to its security:
- Decentralization: No single entity controls the network, reducing the likelihood of centralized attacks.
- Cryptographic Measures: Public/private key cryptography, hash functions, and digital signatures ensure transaction integrity and authenticity.
- Transparency: The transparent nature of the blockchain allows users to audit transactions easily, bolstering trust.
These strengths have made Bitcoin the most recognized and widely utilized cryptocurrency, serving as a benchmark for others.
Weaknesses and Vulnerabilities
Conversely, certain weaknesses can undermine the perceived security of the Bitcoin network:
- Mining Centralization: The consolidation of mining power could leave the network susceptible to a 51% attack.
- Infrastructure Risks: Exchanges and wallets are often target points for DDoS attacks and hacking attempts, impacting user confidence.
- User Responsibility: The reliance on users to manage their private keys can result in significant losses if not handled properly.
Awareness of these vulnerabilities is essential for users, particularly when considering investments in cryptocurrencies.
The Future of Bitcoin Security
Looking forward, Bitcoin security is likely to evolve in response to both technological advancements and emerging threats. Ongoing innovations, combined with an engaged community, pave the way for continued improvements in security protocols.
Ultimately, the inherent strengths of Bitcoin, coupled with active efforts to counteract its vulnerabilities, suggest a promising trajectory for its security and longevity.
Conclusion
In summary, understanding how secure is the Bitcoin network involves examining its decentralized architecture, cryptographic foundations, potential vulnerabilities, and ongoing enhancements. While Bitcoin presents formidable security measures such as public-key cryptography, hash functions, and a transparent blockchain, it faces challenges from mining centralization, potential attacks, and infrastructure risks. Nevertheless, the dynamic nature of the cryptocurrency space fosters continuous development, ensuring that Bitcoin adapts and responds effectively to the ever-evolving landscape of threats. As the world becomes increasingly reliant on digital currencies, vigilance and proactive engagement will be vital to maintaining the integrity and security of the Bitcoin network.